Web Access
Full-featured task management in your browser. Works on any device with zero installation.
Start Free TrialEnd-to-end encrypted. Even we can't see your data.
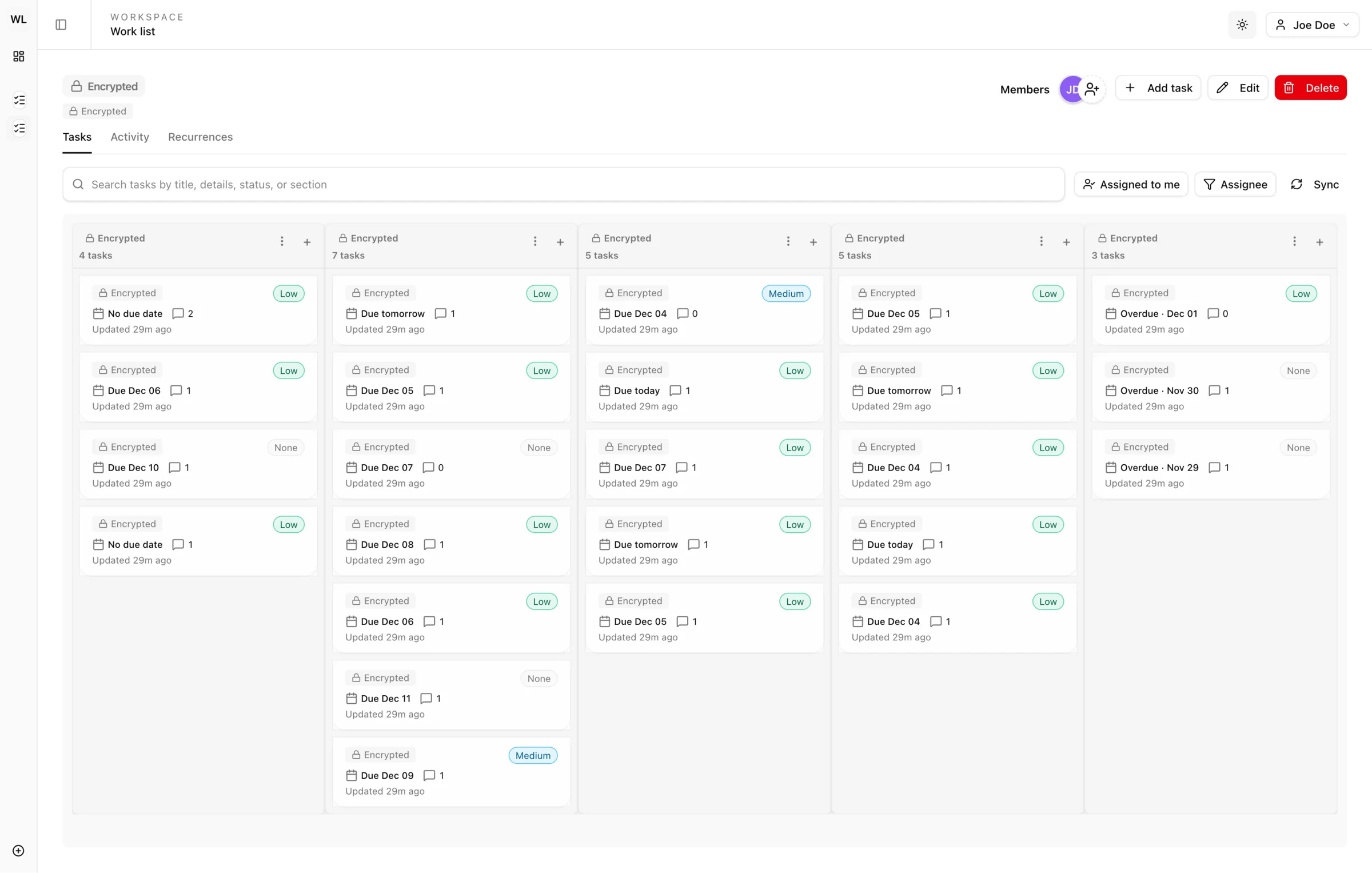
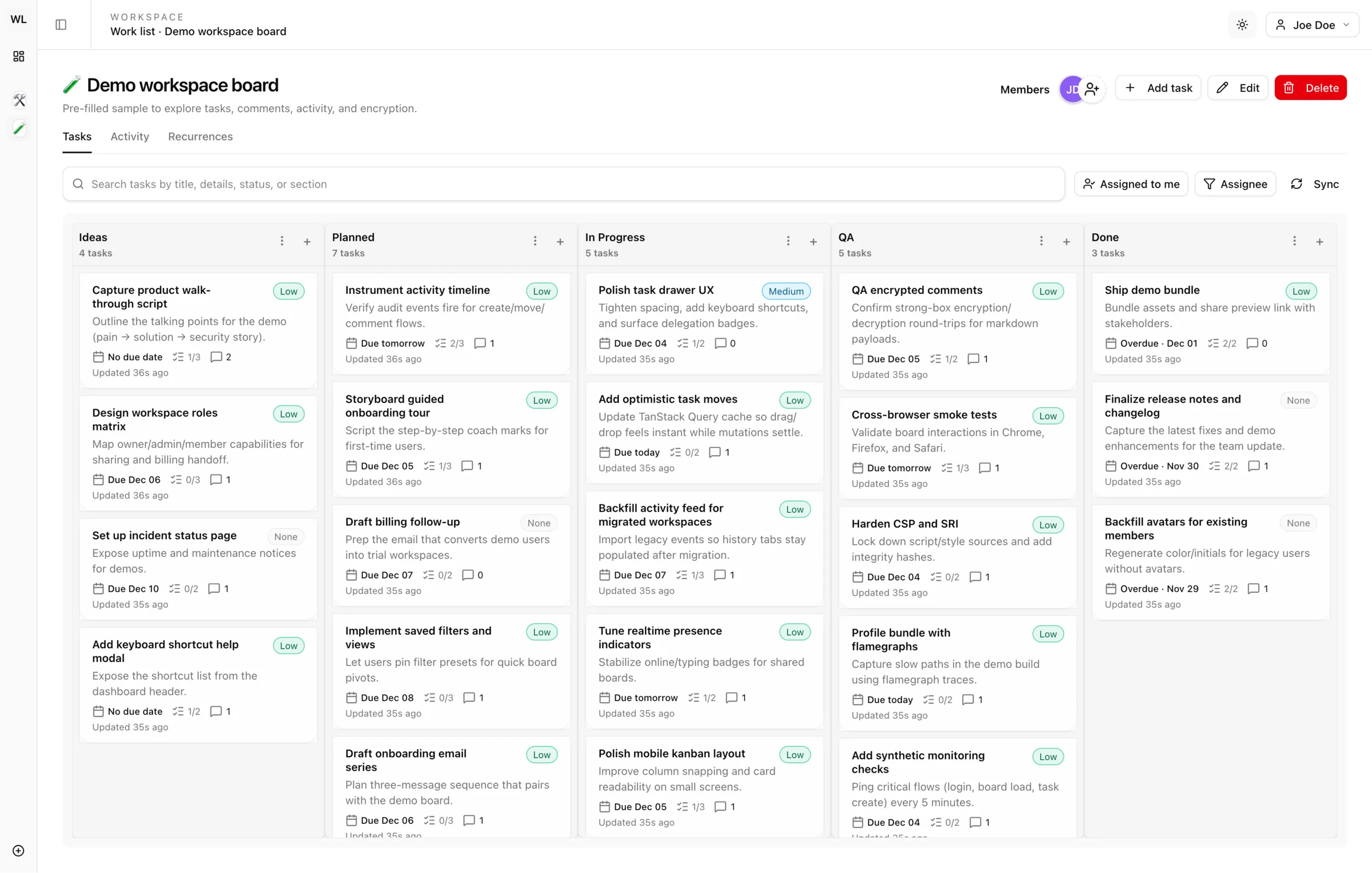
Access your encrypted tasks on the web or iOS. Same security, seamless sync.
Full-featured task management in your browser. Works on any device with zero installation.
Start Free TrialNative iOS app for secure task management on the go. All data encrypted locally.
Every task, every strategy, every client detail you put in traditional productivity tools is readable by someone else—platform employees, third-party integrations, even AI training systems.
When a data breach happens (not if, but when), your entire business strategy becomes public. Yet switching to complex security tools kills team productivity.
There has to be a better way.
Traditional apps store your data in plain text on their servers.
Worklist uses end-to-end encryption—even stronger than online banking. Banks can still access your data; we mathematically cannot. And it's as easy as your favorite task manager.
Your business stays your business
Share securely in seconds
No servers, no setup, no stress
Create your account and start adding tasks immediately. Everything is automatically encrypted in your browser before leaving your device.
Share work lists with team members using secure invitations. They get access to exactly what you share—nothing more, nothing less.
Work together knowing your data is protected by the same cryptography that secures online banking—except even simpler to use.
Every feature is end-to-end encrypted by default.
Owners, priorities, due dates, and progress
Steps for every task, trackable at a glance
Comments, updates, and handoffs
Automate weekly and monthly routines
Private notes, synced across devices
Separate projects, clients, and departments
Every change logged and unreadable to us
Instant results that run in your browser
Work securely from any device
We've built Worklist from the ground up to operate with zero knowledge of your data.
Learn more about our security architectureChaCha20-Poly1305 AEAD, the modern cipher trusted by Signal and Google.
We can't access your data—even if subpoenaed.
Data sovereignty by design—you own and control everything.
Your information is never analyzed, sold, or used for advertising.
Even if our database is breached
→ Your data remains encrypted chunks of gibberish.
Even if we're served a warrant
→ We have no readable data to provide to authorities.
Even if an employee goes rogue
→ They can't decrypt your information without your keys.
Even if you forget your password
→ Your data stays protected (note: there are no backdoors, so recovery keys are vital).
Protect your competitive advantage
Keep product roadmaps, feature specs, and user research away from prying eyes. Perfect for stealth startups and innovation teams.
Client confidentiality, guaranteed
Meet the strictest confidentiality requirements with mathematical certainty, not just policy promises. Ideal for sensitive client work.
Compliance without complexity
Support HIPAA and financial regulations with encryption that exceeds requirements. No expensive infrastructure needed.
Work across borders worry-free
Collaborate globally without data residency concerns. Your encryption travels with your data, protecting it everywhere.
Get 40% off forever when you subscribe within 24 hours
Sign up today and lock in discounted pricing for as long as you stay subscribed
$99.00 $59.4 /year billed yearly
single user · with signup offer
$85.0 $51.0 /seat/year billed yearly
per seat pricing · with signup offer
Billed annually · Minimum 10 seats
Starting at $1000/year
Offer valid for 24 hours after account creation. Regular pricing applies after offer expires.
Collaborate securely with end-to-end encryption. No credit card required.
24-hour window to claim your discount after signup